Continuous, real-time vulnerability detection in application services.
Software Composition Analysis (SCA) is a process and set of tools used to identify and manage open-source components and third-party libraries within software applications.
- Based on the findings of vulnerability and license analysis, SCA tools.
- SCA tools offer guidance on how to remediate identified issues.
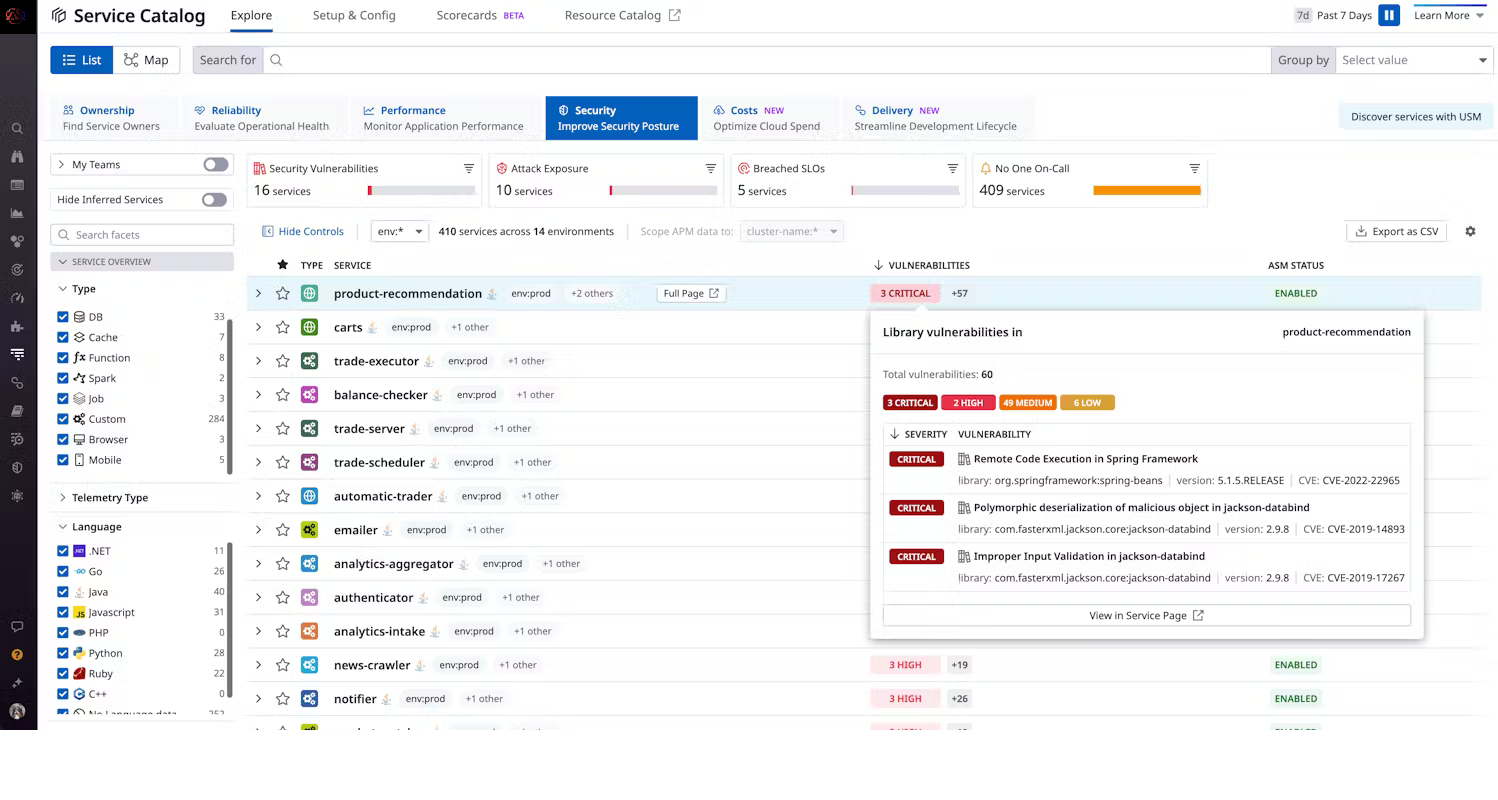
Bigtecsys Software Composition Analysis (SCA) continuously monitors for vulnerable open source libraries in production.
Identify open source security risk in your applications
Identifying open-source security risks in applications involves several key steps and considerations.
Use Software Composition Analysis (SCA) Tools: Employ SCA tools to automatically scan your application and its dependencies for known vulnerabilities. These tools compare component versions against security databases and advisories to identify vulnerabilities and associated risks.
Regular Vulnerability Scanning: Perform regular vulnerability scans using SCA tools as part of your continuous integration (CI) or continuous delivery (CD) pipeline. This ensures that new vulnerabilities are promptly detected as components are updated or new vulnerabilities are disclosed.
Patch and Update Management: Stay informed about security patches and updates for all open-source components used in your application. Regularly update components to patched versions to mitigate known vulnerabilities.

Prioritize vulnerabilities with active risk
Prioritizing vulnerabilities with active risk involves focusing on vulnerabilities that pose the most immediate threat or are actively being exploited. Here are some steps to prioritize vulnerabilities effectively.
Threat Intelligence Integration: Incorporate threat intelligence feeds into your vulnerability management process. These feeds provide information on vulnerabilities that are actively being exploited in the wild or are part of targeted attacks.
Severity and Impact Assessment: Evaluate vulnerabilities based on their severity ratings (e.g., CVSS score) and potential impact on your systems and data. Focus on vulnerabilities with high severity ratings and significant potential impact.
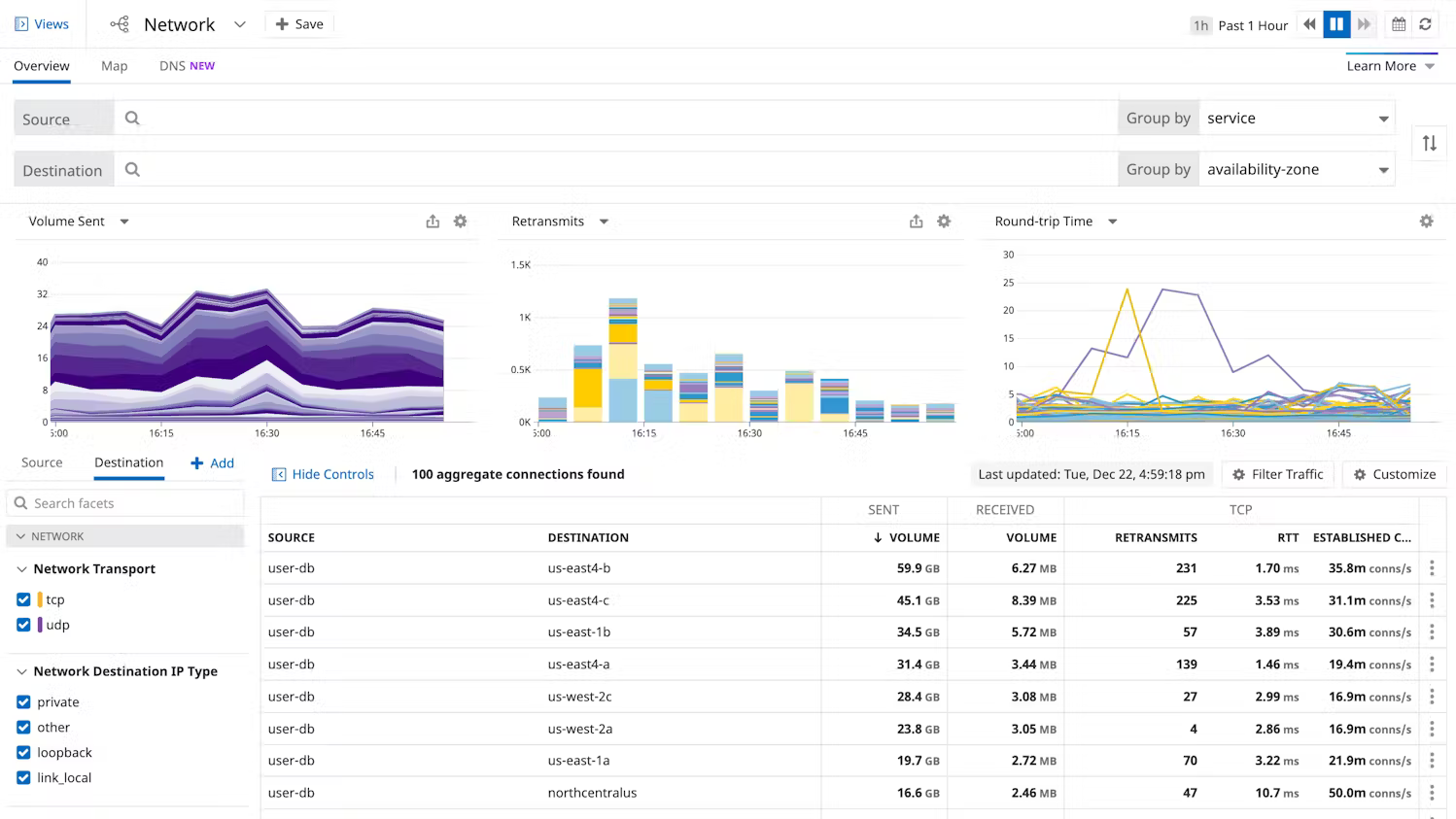
Fast-track resolution with guided remediation
Fast-tracking resolution with guided remediation involves providing actionable steps and support to quickly address and mitigate identified issues or vulnerabilities.
Automated Remediation Workflows: Develop automated workflows that can execute predefined remediation steps for common vulnerabilities or issues. Automation reduces manual effort and speeds up the resolution process.
Integration with Ticketing Systems: Integrate guided remediation workflows with your incident response or ticketing system. This ensures that remediation tasks are tracked, assigned, and monitored throughout their lifecycle.
Validation and Testing: Include validation steps within the guided remediation process to verify that the issue has been successfully resolved. Automated tests or checks can confirm that systems are now secure or operating correctly post-remediation.

Software Composition Analysis (SCA)
Successful cloud migration can transform your organization by offering numerous benefits. Bigtecsys provides tools to benchmark and optimize the performance of on-premises workloads before and after migration, ensuring a smooth and efficient transition
Hybrid Cloud Observability
Self-hosted observability to take you from reactive to proactive across on-prem and hybrid IT environments.
- Deployment to meet your needs, whether behind your firewall or self-hosted in AWS®, Microsoft® Azure, or GCP®
- Flexible licensing – allocate nodes across multiple instances – and optimal scalability
- Built from our years of network management leadership and enhanced with machine learning
Bigtecsys Observability
SaaS-delivered observability to simplify management of cloud-native and hybrid IT environments.
- Visibility across your hybrid IT landscape, including custom apps, microservices, Kubernetes, and containers
- Accelerate insights with unified data across metrics, traces, logs, and user experience
- Extensible with open-source framework, public API, and out-of-the-box third-party integrations
Database Performance Analyzer
Cross-platform database monitoring and management software built for SQL query performance monitoring, analysis, and tuning
- Agentless and designed to be easy to install with quick time-to-value and low overhead of 1% or fewer
- Runs on either Windows® or Linux® servers, in Azure, or as an AWS subscription
- Goes beyond problem analysis by providing expert advice with table tuning and query advisors
Let's Try! Get Free Support
Start Your 6-Day Free Trial
From security to observability and beyond, Bigtecsys helps you go from visibility to action.